POS malware quietly steals customers’ card data, posing as a significant cybersecurity threat that businesses must vigilantly monitor and address.
This malware operates unnoticed, compromising payment information even as businesses maintain seemingly secure operations.
POS malware is alarmingly common, making it crucial for businesses to implement strong preventative measures.
Businesses often end up dealing with the aftermath, shouldering the responsibility to fix breaches and reassure affected customers.
To prevent this sneaky theft, companies must adopt vigilant strategies and robust security practices.
POS malware is the digital equivalent of someone skimming your till while smiling at the camera. It slides in quietly, swipes your customers’ card data, and leaves your team cleaning up the mess with corporate breathing down your neck.
And it’s not rare.
Attackers are actively targeting retail POS systems because—surprise—they work. The tools are cheap. The entry points are everywhere.
And if you’re still relying on outdated software or one-size-fits-none antivirus? You might as well hang a welcome sign.
This guide is your BS-free breakdown of how POS malware works, what flavors it comes in, and how to spot the warning signs before your CFO starts hyperventilating.
What is POS Malware?
POS malware is code built to jack your point-of-sale systems and skim payment data straight from memory—before it ever gets encrypted or sent off for processing.
It runs silent, hits fast, and ships stolen card info to whoever paid for the exploit.
You won’t get flashing alerts or dramatic warning screens. Most businesses don’t notice anything until the damage is done—fraud reports roll in, banks start calling, and you’re suddenly the subject of a breach notification nobody wants to write.
If customer data moves through your terminals, you’re a target. The question isn’t if attackers will try—it's whether they'll find an opening.
11 Types of POS Malware Attacks
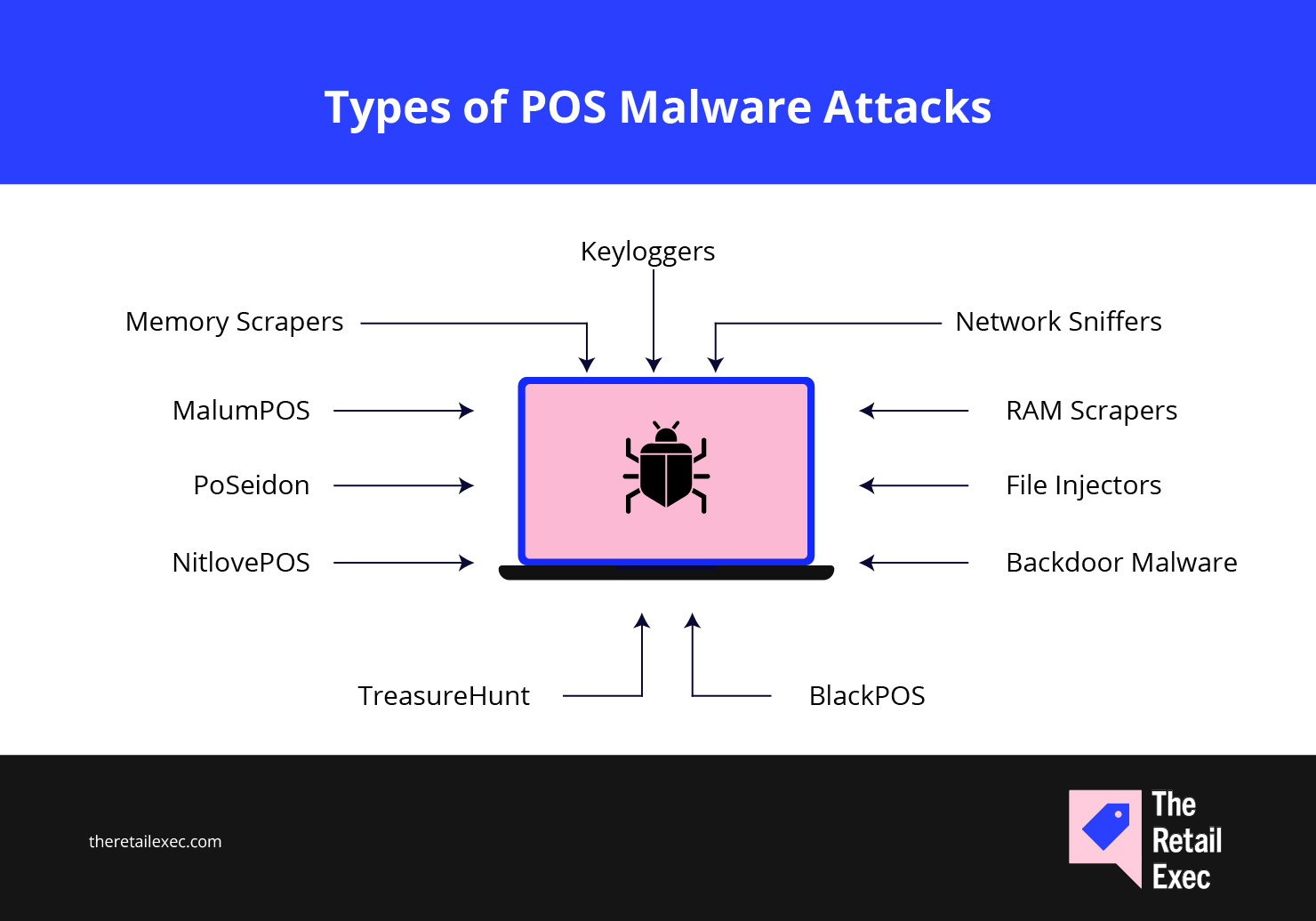
POS malware isn’t one-size-fits-all. It comes in flavors—each designed to exploit a different gap in your system. Some hover in memory. Others log every key you press. A few pretend to be legit software while quietly exfiltrating card data.
Let’s start with one of the all-time greatest hits.
Memory scrapers
Memory scrapers sit in your POS terminal’s RAM and wait for unencrypted card data to pass through. When a customer swipes or dips their card, there’s a split second before that info gets encrypted—scrapers grab it right then. Clean. Quiet. Gone.
The stolen data is exfiltrated in batches to a remote server—usually encrypted to avoid detection. You won’t see a thing unless you’re actively looking for unusual memory behavior, which—let’s be honest—most aren’t.
These scrapers are why endpoint protection alone won’t cut it. If your systems aren’t built to detect in-memory threats, you’re flying blind.
Keyloggers
Keyloggers track everything typed into your POS systems—PINs, passwords, admin logins, even those secret “fix-it” codes your IT guy swore only he knew.
They’re either installed via malware-laced files or physically plugged into your point-of-sale terminals. Both versions work just fine for cybercriminals.
Once embedded, the keylogger quietly records keystrokes and sends them to a command-and-control server.
From there, hackers can launch secondary attacks, pivot across your network, or just sit back and enjoy the stream of freshly captured customer data and authentication credentials.
Keyloggers often ride in on phishing emails or compromised POS software updates. And because they don’t need to scan memory or intercept network traffic, antivirus tools can easily miss them—especially if you’re still relying on outdated endpoint security.
One more reason to train your team like they’re part of the cybersecurity squad—and not just there to ring up socks and smoothies.
Real-world hit:
In 2015, Chili’s restaurants discovered their POS terminals had been infected with keylogger malware.
More than 60 locations were affected, leaking credit card data and forcing the company into damage control mode—including customer notifications and credit monitoring services.
Network sniffers
Network sniffers don’t care about what’s happening inside your POS terminal—they care about what’s flying through the wires.
These malware variants intercept unencrypted payment card data as it travels between your POS devices and the payment processor. If you're not encrypting that traffic? They're all ears.
Sniffers lurk in your network stack, watching for magnetic stripe swipes, chip reads, and manual entries.
And if you’ve got poor segmentation, weak firewall rules, or unsecured third-party integrations? You’ve basically handed them a front-row seat.
This kind of malware doesn’t need to break into your point-of-sale software or scrape memory—it just waits for payment information to roll by. And if your network security hygiene is spotty, it doesn’t take long to collect a jackpot of credit card information and cardholder data.
Real-world hit:
In 2019, Hy-Vee discovered a data breach across several of its operations—including gas pumps and restaurants—thanks to a network sniffer capturing payment card data in transit.
Poor network segmentation gave the malware free rein across their POS environment.
RAM scrapers
RAM scrapers go straight for the system’s memory—specifically, the random-access memory inside your POS terminals. That’s where unencrypted payment card data briefly lives right after a card is swiped or dipped, and before it gets handed off for processing.
Unlike memory scrapers that zero in on specific card data fields, RAM scrapers sweep up a much broader set—credit card numbers, expiration dates, names, and even full transaction details.
The stolen data is bundled and sent off to remote servers for later resale or fraud use.
These threats are especially dangerous in multi-location retail chains running identical POS software across stores. A single successful infiltration can lead to wide-scale exfiltration of customer data before anyone notices something’s off.
Modern scrapers are built to avoid detection by antivirus tools and blend in with normal system functionality.
Without robust monitoring in place, they can live in your system for weeks—maybe longer.
File injectors
File injectors don’t just sneak in—they move in.
This malware modifies legitimate POS software files by injecting malicious code into them. On the surface, everything looks fine. Your POS system boots up, runs as expected, and no one suspects a thing.
Meanwhile, that injected code is quietly doing its thing—stealing credit card data, altering transaction records, or creating remote access points that let attackers stroll in anytime they want.
Worse? Because it’s piggybacking on legitimate POS system files, traditional antivirus tools often let it pass. It's like hiding a trojan inside a receipt printer update—except this one phones home with customer payment data.
POS malware families like NitlovePOS and MalumPOS have used this tactic with frightening efficiency—especially in environments running outdated or poorly patched operating systems.
Backdoor malware
Backdoor malware is exactly what it sounds like—an invisible side entrance planted in your POS system so cybercriminals can waltz in anytime, no knocking required.
Once installed, backdoors give attackers persistent remote access to your POS environment.
They can move laterally across your network, exfiltrate credit card data, drop additional malware variants, or just sit tight until they’re ready to strike. And since it all happens in the background, your team usually doesn’t spot it until after the data breach report is already circulating.
These threats often sneak in via compromised software updates, weak third-party integrations, or poorly secured remote access tools—looking at you, outdated remote desktop protocols.
Real-world hit:
In 2018, Applebee’s got stung by a backdoor malware attack that exposed payment card information at over 160 locations.
The attackers maintained access for weeks before the breach was discovered, proving once again that "set-it-and-forget-it" POS security is a myth.
BlackPOS
BlackPOS isn’t just another memory scraper—it’s the blueprint for high-impact retail cyberattacks.
Built to siphon credit card data directly from POS terminals, it specializes in stealth, speed, and staying power.
This malware doesn’t just harvest card numbers—it dodges detection while doing it. With techniques like code obfuscation and anti-analysis hooks, BlackPOS hides in plain sight, bypassing many antivirus and endpoint security tools like they’re not even there.
It doesn’t care if you're running the latest POS software or have a firewall in place.
If your point-of-sale systems have any vulnerabilities—especially in their memory handling or network security—BlackPOS knows how to exploit them.
Real-world hit:
BlackPOS was the star of the 2013 Target breach, which exposed over 40 million payment card records and cost the company an estimated $292 million. It entered via a third-party HVAC vendor and moved through the network until it hit POS gold.
TreasureHunt
TreasureHunt is a classic "low and slow" POS malware variant.
It combines memory scraping and keylogging to collect payment card data and customer information without setting off alarms. If it’s in your system, it’s not rushing—just quietly harvesting and exfiltrating over time.
Designed for stealth, this malware family uses code obfuscation, anti-debugging techniques, and minimal system disruption to keep a low profile.
That means fewer red flags for your IT team—and more time for attackers to grab credit card info before anyone notices.
TreasureHunt is often found lurking in unpatched point-of-sale systems or bundled into trojanized software updates. And like its pirate-themed name suggests, it’s all about stealing your buried (payment card) treasure without triggering a mutiny.
NitlovePOS
NitlovePOS doesn’t make a flashy entrance—it blends in, burrows deep, and sticks around.
This malware injects itself into legit POS software, quietly siphoning off payment card data while pretending to be just another background process.
It’s especially effective on outdated or unpatched operating systems, where it can slip past basic security checks unnoticed. Once inside, NitlovePOS exfiltrates credit card information over time—small, steady, and under the radar.
Because it hides inside trusted files, it’s tough to detect without whitelisting or file integrity monitoring.
If you're not actively checking what your point-of-sale software is doing under the hood, you may never know it’s been compromised.
PoSeidon
PoSeidon doesn’t just show up and start scraping—it infiltrates, evolves, and upgrades itself as it goes.
It usually gets in through phishing emails or compromised websites, then digs into your POS terminals to hunt for credit card data in memory.
But PoSeidon doesn’t stop at memory scraping. It also focuses on Track 1 and Track 2 data from magnetic stripe cards—which includes card numbers, expiration dates, and cardholder names.
Then, like a good little malware overachiever, it wipes its tracks after exfiltration, making forensic cleanup a nightmare.
It’s modular, too. Once PoSeidon is installed, it can download additional payloads to extend its functionality—think trojans, keyloggers, or even ransomware, depending on the attacker’s goal.
MalumPOS
MalumPOS is less a piece of malware and more a toolkit—for hackers who want to pick and choose how they mess with your payment systems.
It’s modular, which means attackers can load it up with whatever data-stealing features they need: memory scraping, keylogging, network sniffing, you name it.
It’s also designed to target a wide range of point-of-sale systems, not just one specific platform. Retailers using Oracle MICROS, for example? MalumPOS has been tailored specifically for that.
It’s flexible, adaptable, and constantly updated to stay ahead of antivirus software and detection tools.
Once inside your POS environment, it can spread across devices, steal credit card data in bulk, and send it out through encrypted channels—often without tripping any alerts.
How POS Malware Works: 5 Steps
Whether it’s scraping memory, logging keystrokes, or sniffing network traffic, most POS malware follows the same basic playbook. Here’s how these attacks usually go down—start to finish.
1. Infiltration
First, the attacker gets in.
Maybe it’s a phishing email an employee clicked, a trojanized POS software update, or a compromised vendor connection. However it happens, the goal is to land malware inside your retail network without raising alarms.
Unpatched operating systems, poor firewall rules, and flat networks make this part way too easy.
If you’re not locking down remote access points or filtering what can run on your POS devices, this is where the party starts.
2. Residence
Once inside, the malware digs in.
It hides inside system memory, injects itself into POS software, or creates backdoors for easy re-entry. Most variants use obfuscation and anti-analysis techniques to stay hidden from your antivirus and monitoring tools.
This phase can last days—or months. And the longer the malware sits undetected, the more damage it can do.
3. Operation
This is where the real damage begins.
The malware activates its core functionality—scraping memory, logging keystrokes, sniffing traffic, or copying files—depending on the variant.
If you’re not watching for behavioral anomalies or actively scanning your POS terminals’ random-access memory, you probably won’t notice anything out of the ordinary.
4. Data exfiltration
Once it’s collected enough credit card information and customer data, the malware sends it off to a remote command-and-control server.
Most attacks use encrypted channels and throttle the data to avoid triggering bandwidth alarms.
The result? Payment card data, debit card numbers, expiration dates, and personal information—leaked without anyone noticing. Sometimes for weeks.
5. Persistence and spread
Good malware doesn’t leave when the job’s done. It sticks around.
It may re-infect systems after you “clean” them, or move laterally to other point-of-sale terminals or systems in your environment.
This is where retailers get hit hardest.
One infected POS device becomes five. One store becomes twenty. One breach becomes a nationwide issue—and now your compliance, PR, and legal teams are all looped in.
POS Malware Risk Factors for Businesses: 9 Signs You're Exposed
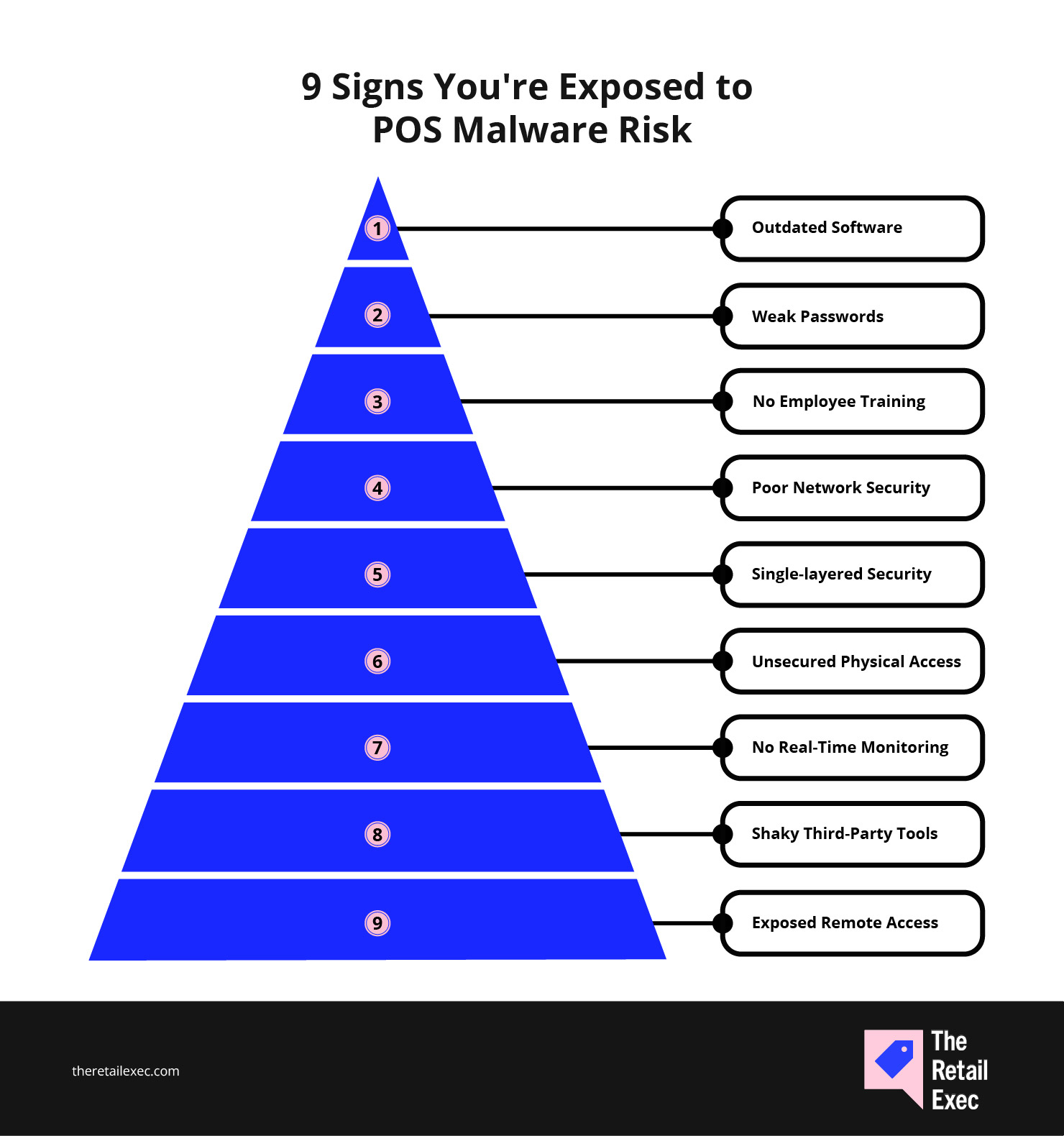
These aren’t just theoretical slip-ups—most of the high-profile retail breaches in the past decade started with one or two of these weak points. Spot them early, and you’ve already won half the battle.
- Outdated software. Running old versions of your POS software or operating system makes you a magnet for known exploits—especially if you’re skipping patches and updates.
- Weak passwords and default credentials. If you’re still using “admin” or haven’t forced a reset since 2019, you’re handing out free access to cybercriminals.
- No employee training. Your POS system is only as secure as the person using it. If staff can’t spot phishing, social engineering, or shady pop-ups, that’s a serious vulnerability.
- Poor network security. A flat network with no segmentation, weak firewall rules, and wide-open access gives malware a clear path from one system to the next.
- Single-layer security. Antivirus alone won’t cut it. If you’re not layering protections—endpoint detection, real-time monitoring, application whitelisting—you’re flying blind.
- Unsecured physical access. Anyone who can plug a USB stick into a POS terminal can install malware. Lock down devices, ports, and access like your data depends on it.
- No real-time monitoring. If you’re only checking logs after something goes wrong, you’re already too late. Real-time alerts give you a shot at catching threats early.
- Shaky third-party integrations. Vendors and plugins that touch your POS systems can introduce vulnerabilities. If they’re not secure, neither are you.
- Exposed remote access tools. Remote desktop access is convenient—but if it’s not locked down with multi-factor authentication and IP restrictions, attackers will find it first.
If you’re checking off more than a couple of these? It’s probably time for a retail cybersecurity gut check.
Impact of POS Malware on Businesses and Customers
When malware hits your POS systems, it’s not just a tech issue—it’s a business disruption, a trust killer, and a financial black hole. Here’s what’s at stake:
- Financial losses. From direct theft to breach recovery costs, POS malware drains budgets fast. Expect to pay for investigations, legal fees, card reissuance, and possibly compliance fines. For smaller retailers, a single breach can be lights out.
- Reputation damage. Word spreads fast—especially when customer credit card data is involved. One breach can undo years of brand building and kill customer loyalty overnight.
- Operational disruption. Malware often means shutting down POS terminals to contain the threat. That leads to lost sales, frustrated customers, and a cascading mess across inventory, staffing, and back-office systems.
- Legal and regulatory fallout. If your payment card data protections don’t meet PCI DSS or regional privacy laws, you’re looking at audits, fines, and maybe lawsuits. No one wants to be the test case for non-compliance.
- Customer financial risk. Stolen card data leads to fraudulent charges and drained accounts. Even if banks cover the losses, your customers associate the hassle—and the breach—with your brand.
- Identity theft. If attackers exfiltrate more than just card numbers (think names, billing addresses, phone numbers), customers may face long-term damage from identity fraud.
- Loss of trust. This is the gut punch. Customers expect point-of-sale systems to be secure. Once that trust is broken, it’s hard to earn back—and some may never return.
- Privacy concerns. Beyond card data, many POS systems hold customer info like purchase history and contact details. When that gets out, customers feel exposed—and your privacy policies suddenly get a lot more scrutiny.
How to Protect Your Business Against POS Malware: 14 Actionable Strategies
Good news: POS malware is preventable. Bad news: it takes more than an antivirus subscription and a locked drawer.
If you're serious about protecting your point-of-sale systems, customer data, and brand reputation, you need a layered defense plan that works in the real world—not just on a compliance checklist.
Here's where to start.
1. Update your POS software and systems regularly
Patch your POS software, operating systems, and third-party tools the second updates are available.
Cybercriminals don’t need zero-day exploits—they just need you to be lazy with your updates.
Create a formal patch management schedule and assign clear ownership. If it touches customer data, it needs eyes on it.
2. Enforce strong passwords and lock down access
No shared logins. No “store1POS” passwords.
Enforce strong, unique passwords for every POS account, rotate them regularly, and enable multi-factor authentication wherever possible.
Limit admin privileges to people who actually need them—and audit access logs like you mean it.
3. Train employees to spot cyberattacks before they spread
Your POS system is only as secure as the person using it. If your team can’t recognize a phishing email, a fake update prompt, or a shady USB drop, you’re leaving the door wide open.
Train front-line staff, store managers, and even HQ ops teams to recognize red flags—social engineering, weird pop-ups, and fake tech support calls.
Keep it short, regular, and practical. This isn’t about turning them into cybersecurity experts—it’s about keeping them from becoming the breach.
4. Segment your network like it’s your storefront layout
If everything’s connected to everything, one infected POS terminal can take down your entire retail operation.
Create separate networks for your POS systems, guest Wi-Fi, back-office tools, and third-party integrations.
Use firewalls to control what traffic moves between zones. If you wouldn’t let someone from the food court walk into your stockroom, don’t let your loyalty program have direct access to your POS.
5. Use anti-malware tools that actually detect modern threats
POS malware has evolved—and if your antivirus hasn’t, you’re not protected. Look for enterprise-grade tools that go beyond signature scans.
You want memory scanning, behavior-based detection, and machine learning that can flag suspicious activity in real time.
And yes, it needs to be monitored. Installing antivirus and calling it a day is like locking the front door and leaving the windows wide open.
6. Encrypt payment data at every stage
If malware does get in, encryption can stop it from stealing anything usable.
Encrypt payment card data at rest, in transit, and anywhere else it touches—from the POS terminal to the payment processor.
Use strong encryption protocols (like AES-256), manage your keys securely, and never assume encryption alone is enough. It's one layer in a multilayer defense—not a get-out-of-breach-free card.
7. Limit who can access POS systems (physically and digitally)
Only give access to people who need it—and even then, only what they need.
Use role-based access controls (RBAC) to restrict permissions, and enforce multi-factor authentication on all POS admin accounts.
On the physical side, lock down terminals, restrict USB ports, and keep hardware where customers (and randoms) can’t tamper with it. If someone can walk up and plug in a flash drive, you’ve got bigger problems than card skimming.
8. Monitor POS activity in real time—not once a month
If you’re relying on log reviews or after-the-fact audits, you’ll catch malware right after it’s already done the damage.
Set up real-time monitoring with alerts for suspicious behavior—like unusual memory usage, unauthorized logins, or traffic heading to known bad IPs.
Hook your POS devices into a SIEM or other centralized monitoring tool so you can correlate weird behavior across systems. If one terminal gets hit, you want to catch it before it spreads to ten more.
9. Build an incident response plan before you need one
Don’t wait for a breach to figure out who’s doing what. Map out exactly how your team will respond to a malware attack—from detection to containment to customer notifications.
Your plan should cover:
- Who investigates
- How to isolate infected POS systems
- When to pull the plug (literally)
- Who talks to legal, PR, and customers
Test it. Update it. And make sure everyone—from HQ to store managers—knows where to find it without digging through a 42-tab spreadsheet.
10. Run regular audits and stay PCI-compliant
Compliance isn’t exciting, but it’s non-negotiable.
Schedule routine audits to ensure your POS setup meets data security standards like PCI DSS. If you’re not checking for gaps, attackers will.
Work with a qualified security assessor if needed. Document everything—because when the regulators (or lawyers) come calling, “we think it was fine” won’t cut it.
11. Secure your physical POS environment like it matters
Cybercriminals love unattended terminals and exposed hardware. Lock down your POS devices physically—install them in secure mounts, disable unused ports, and use tamper-evident seals.
And no, backroom break rooms are not “secure storage.”
If someone can walk up to a terminal with a USB stick or card skimmer, they don’t need hacking skills—they just need 30 seconds alone.
12. Vet your third-party vendors like they’re part of your team
If a third-party service plugs into your POS—payment gateways, loyalty platforms, inventory systems—it’s part of your risk profile.
Ask hard questions about their cybersecurity posture, demand compliance proof, and bake security requirements into your contracts.
Remember: Target’s breach came through an HVAC vendor. Don't assume your integrations are clean just because they have a nice pitch deck.
13. Deploy advanced tools for smarter defense
Go beyond antivirus. Modern POS malware is built to dodge signature-based detection—so you need tools that look at behavior, not just file names.
- Use endpoint detection and response (EDR) to monitor what’s happening on your POS terminals in real time.
- Deploy intrusion detection systems (IDS) to watch network traffic for signs of command-and-control activity or data exfiltration.
- And enable application whitelisting to make sure only approved software can run—if something new shows up uninvited, it doesn’t get through.
- Bonus points if your stack includes memory scanning and anomaly detection built around machine learning.
The goal isn’t to stack a bunch of tools—it’s to build layered visibility into what’s happening across your POS environment before, during, and after an attempted breach.
14. Back up everything—and know how to restore fast
Backups won’t stop a malware attack, but they’ll help you bounce back faster. Create secure, offline backups of POS configurations, software, and transaction data.
Test your recovery process regularly so you're not figuring it out mid-crisis.
A backup that’s never tested is just a false sense of security. Treat your recovery plan like part of your store playbook—not just an IT chore.
Bullet-Proof Your POS Defenses Against Malware
POS malware isn’t slowing down. If anything, it’s getting sneakier—hiding in memory, slipping through third-party vendors, and bypassing the basic antivirus setups too many retailers still rely on.
But this isn’t a panic moment. It’s a readiness one.
With the right layered strategy—technical, operational, and human—you can keep your systems clean, your customer data safe, and your stores running without interruption. It’s not about locking down everything forever. It’s about making it really, really hard for attackers to win.
And if you’re not sure where your biggest gaps are? Start with the list above. Fix one thing. Then another. And keep going.
Retail never stands still—and neither should you. Subscribe to our newsletter for the latest insights, strategies, and career resources from top retail leaders shaping the industry.


